Research
The following highlights the research I have been involved in. If you prefer, you can go straight to my publication list, instead.
🕵️ Anonymous credentials
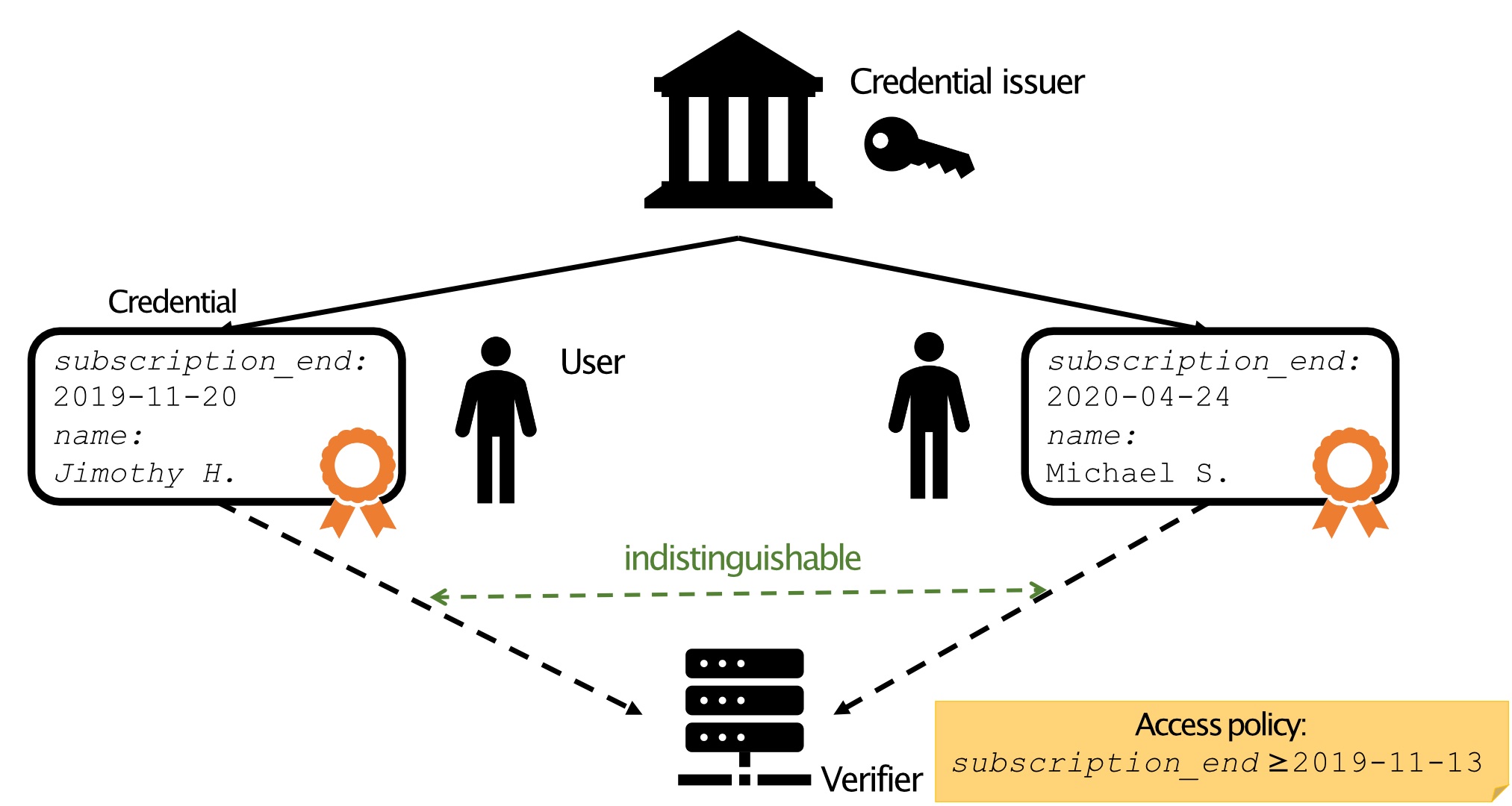
In contrast to username/password authentication, anonymous credentials can be used for authentication without telling the service who you are. Later, we realized that they are even more powerful than that. Anonymous credentials can be used to store arbitrary authenticated data with the user (instead of having to store all data on a server). Using zero-knowledge proofs, users can then prove statements about their data to services, instead of having to reveal the data in plain.
With 📄 updatable credentials, services can even update the user’s data without seeing the data. This enables a whole host of applications that can operate completely blind to their users’ data.
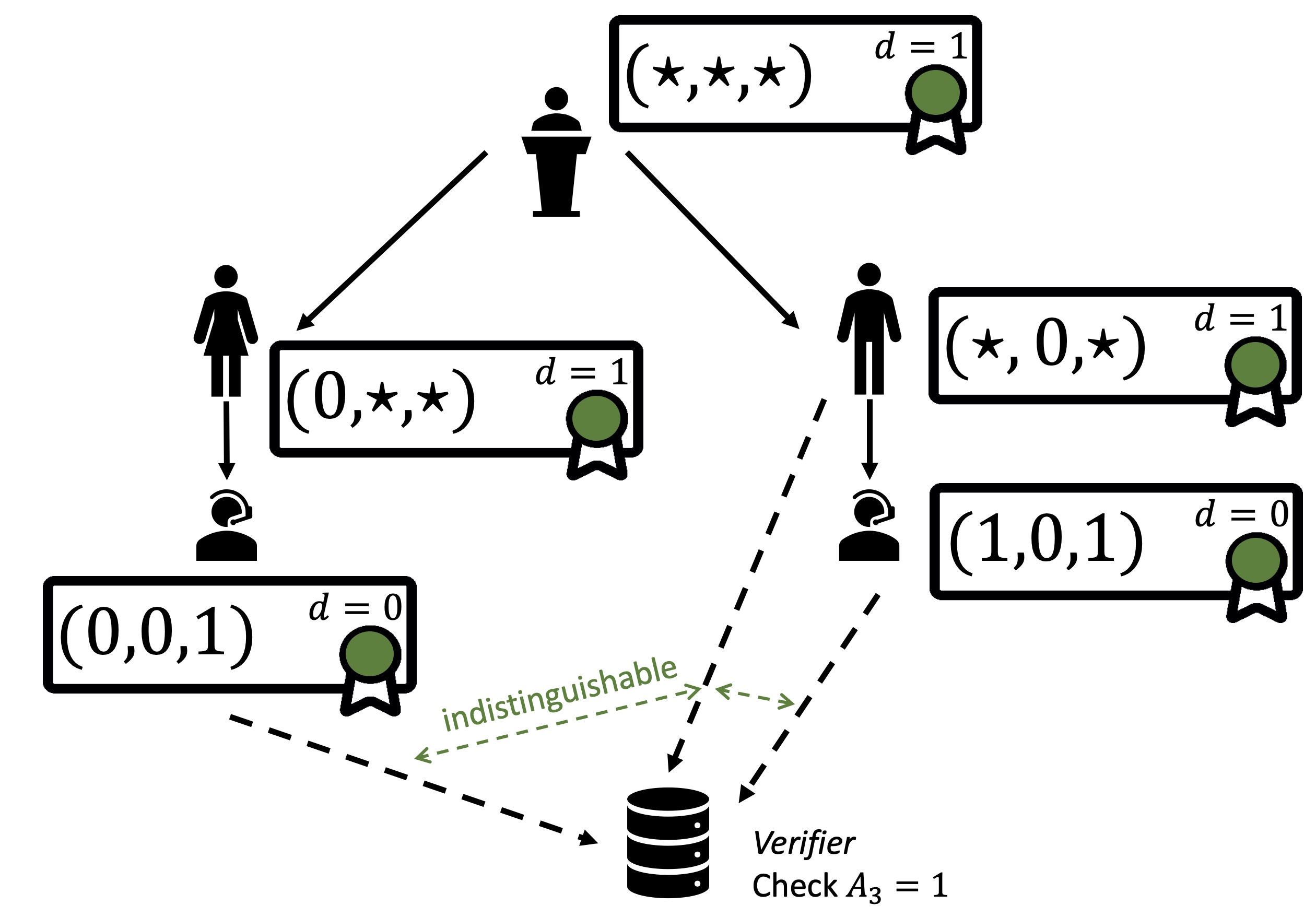
We’ve come up with a special signature scheme, namely 📄 dynamically malleable signatures. With those, we can allow users to delegate weaker versions of their credentials to other people.
With the help of a student project group, we have 📄 implemented a basic anonymous credential system, and noticed that with sufficiently powerful anonymous credentials, you get a basic anonymous reputation system for free.
Usually, when presenting credentials, you have to disclose who issued the credential, which can reveal lots of information. This issue can be circumvented with 📄 delegatable credentials or, more generally applicably, 📄 issuer-hiding anonymous credentials.
💳 Anonymous point collection systems
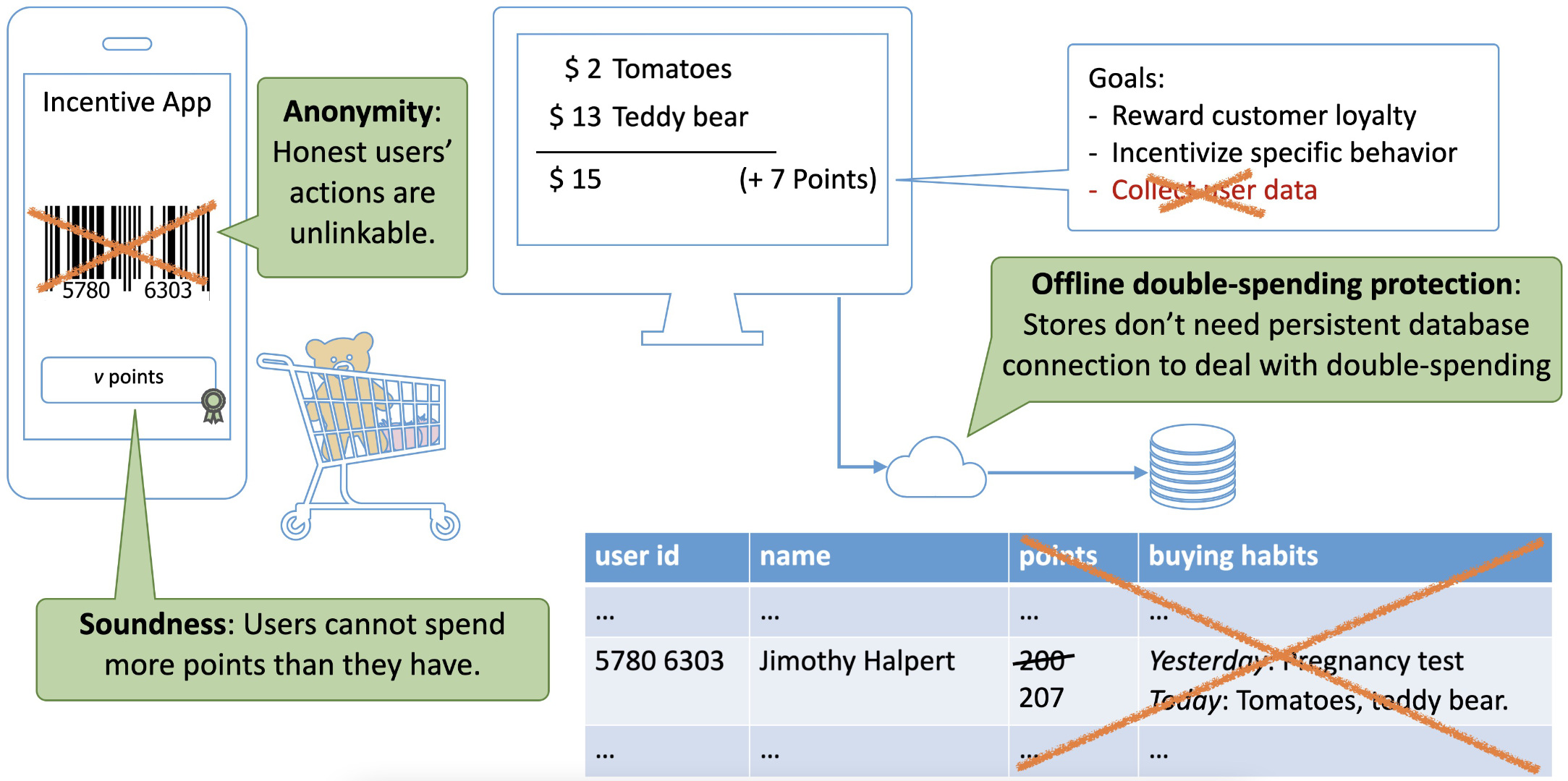
A particularly nice application of the idea of having users store their own data are point collection systems. Users store an authenticated point count that can be anonymously incremented or decremented. Generally, these systems have users incrementally collect points (e.g., whenever I spend bucks in the store, I get points) and then spend those points for rewards (e.g., exchange points for a free teddy bear 🧸).
We designed such a system using 📄 updatable credentials, resulting in a flexible blueprint for anonymous point collection systems.
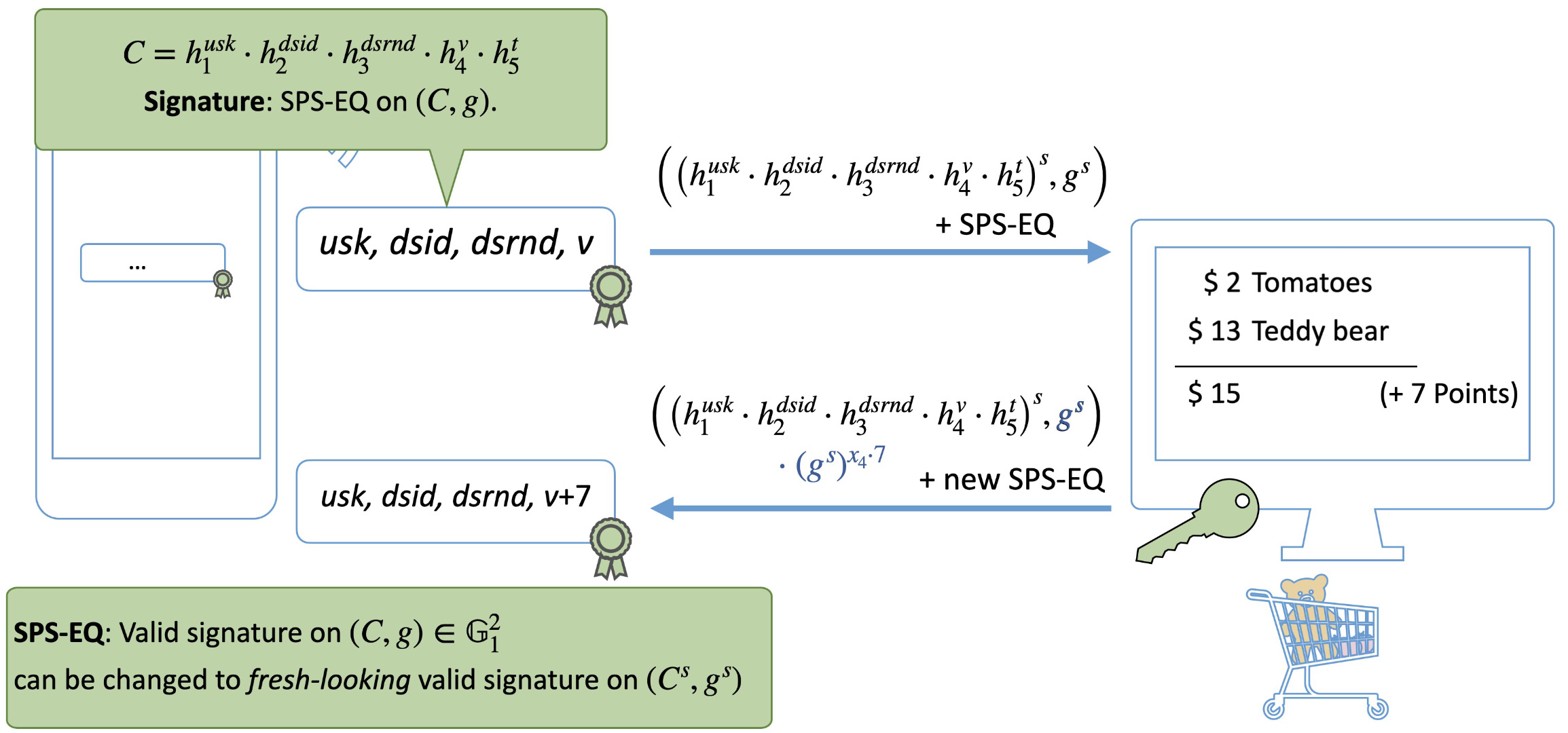
We then improved upon efficiency, enabling efficient point earning protocols 📄 without zero-knowledge proofs. The trick: use structure-preserving signatures on equivalence classes (SPS-EQ) instead of zero-knowledge proofs. This idea almost made it into practice. Also, security is now much better, getting robustness against protocol aborts and secret leakage.
Finally, within a DFG SFB 👔 transfer project and with our industry partners at Diebold Nixdorf, we are 🧑💻 building a real-world prototype of an anonymous point collection system. The implementation is powered by our own library, Cryptimeleon (see below). It is mostly done by our two student assistants.
🧑💻 Implementation of privacy-preserving cryptography
We have created a library for fast prototyping of privacy-preserving cryptography: 🦎 Cryptimeleon. It makes it easy to implement Schnorr-style protocols and it does some useful automatic optimization for benchmarking (see 📄 paper).
Cryptimeleon has been used to implement several of our papers (such as issuer-hiding credentials, updatable credentials), and an anonymous point collection system (see above).
For easy implementation of Schnorr-style protocols, we have implemented the compiler 🥶 Subzero, which takes a Camenisch-Stadler notation proof and turns it into Cryptimeleon code. Subzero was designed and implemented by a DAAD RISE stipend student.
👁 Anonymous communication
We asked ourselves: if every computer had a trusted execution environment, could we do proper anonymous communication over an untrusted network suitable for absurd levels of paranoia? Turns out, the answer is yes*. It’s not cheap, though.
This resulted in a construction bringing together ideas from reconfigurable overlay networks and some (basic) cryptography. So far, we have not published the result, but a draft is available upon request.